Backdooring a HID Reader
A while back, I bought a HID Prox Pro II on eBay for some long-forgotten experiment — likely this. Outside of being well documented and cheaply available, @shakataganai wrote a fantastic article about how to connect it to an Arduino, which makes it ideal for some testing.

While exploring the device, I was disappointed that the actual components of the device (except the antenna) were sealed under some type of resin coating. Despite the components being inaccessible, I noticed there was a lot of available space inside…Big enough to fit an entire Proxmark3. So — theoretically, it may be possible to install a device inside this empty space that could capture tag data whenever someone swipes.


Feedback from folks on Twitter noted the potential for interference between the two devices — which makes sense, if the HID card reader is emitting a signal to power a card, a second device in close proximity could cause a problem.
The argument is sound, I’d previously experimented with an Anti-NFC card from CN360’s Unicorn team, which emits a signal to jam communication between a reader and a tag.
A possible way to get around this came from NotMedic and iceman was to possibly wire the Proxmark to the device’s physical antenna.
From looking at the inside of the HID device, it wouldn’t be terribly hard to solder a lead to the exposed antenna connection — using an alligator clip may be faster.

However, I wasn’t feeling bold enough to go that route, and opted to use the stock antenna and test things out. From the Proxmark client, I was able to verify readability of my testing tag/card.
proxmark3> lf search NOTE: some demods output possible binary if it finds something that looks like a tag False Positives ARE possible
Checking for known tags:
HID Prox TAG ID: 2e6277a2df
--------------------------------------------------
Format: C1k35s (HID Corporate 1000 35-bit standard layout)
Facility Code: 787
Card Number: 774511
Parity: Valid
--------------------------------------------------
Valid HID Prox ID Found!
Using
lf snoop, the device will eavesdrop in on the tag reads from the HID reader:proxmark3> lf snoop proxmark3> data sample Reading 39999 bytes from device memory
Data fetched Samples @ 8 bits/smpl, decimation 1:1 proxmark3> data plot
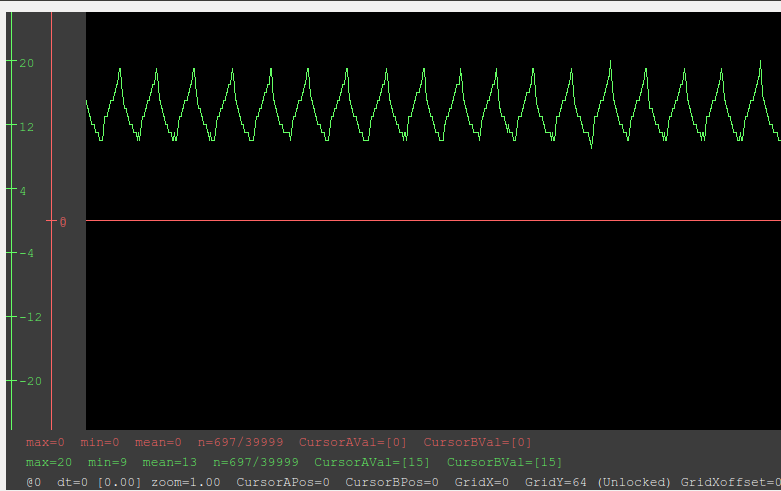
Practicality
While a nifty trick there are some practicalities that make conducting this a challenge:
- Tamper sensors — as mdhardeman pointed out many HID readers have either optical or switch based tamper sensors to alert if someone attempts this.
- Space & Power— While Proxmark fits, I needed to run a USB cable out the back for power/comms, which was tricky. Use in the field may be better using something like a ESP-RFID-Tool, as pointed out by jermainlaforce. Despite the ESP-RFID-Tool having a smaller footprint, it uses wifi — which unless carefully planned, could lead to having to physically be close to the backdoored HID reader.
(Post migrated from Medium - https://medium.com/emptyregisters/backdooring-a-hid-reader-22a9cc9bd92b )


Comments
Post a Comment